Introduction
In my last blog article, we took a look at an old friend – network security and micro segmentation – and how it takes place in modern times. Setting aside this old but gold approach, let’s travel back to the future and take a look at newer Network Security technologies.
In times of web-based applications and services, availability and performance are indispensable factors. To ensure the needed availability and performance you must distribute and control requests or traffic and protect your web-based applications and services.
Back to the Future
The rise of smartphones and mobile devices leads to an evolution in the applications and services landscape. Applications and services shift from local installation to the web to fulfil the requirements of the modern world. They are available from every location, at every time and for every device. This evolution can be overwhelming and aside from its great possibilities, it also exposes applications and services to new ways of being attacked and interrupted.
With the paradigm shift of applications and services, threats and attacks have changed too!
Today, you don’t need to break into a local device or place your malware in a network to create chaos. You only need compute power (which you can rent) and a network connection to start attacking web services and applications.
There are many different types of attacks in the contemporary threat landscape which try to make your life difficult. Attackers can attack open ports and vulnerable software, but the most popular type of attack is the distributed denial of services attack (DDoS).
“I guess you guys aren´t ready for that yet. But your kids are gonna love it“ – Marty McFly
1.21 Gigawatts?
A Distributed Denial of Service (DDoS) attack attempts to interrupt the availability and connectivity of a web service or application. Attackers utilize different sources (mostly compromised systems) to flood the victim. Perpetrators can buy DDoS as a service or rent computing power to perform these types of attack. Anyone with money can do it!
But no worries – there are ways to protect your services and applications in the Azure Cloud.
Azure DDoS Protection
In the Azure Cloud, your infrastructure is protected by default with DDoS (Basic) Protection at no additional cost. No configuration or application changes are needed; it’s as easy as buying a DDoS as a service bundle.

– Source: Microsoft
The DDoS Basic Tier comes with “active traffic monitoring & always on detection” and “automatic attack mitigations” features and provides defense against common network-layer attacks. If a DDoS attack hits you, traffic is automatically blocked, and the remaining traffic is redirected to its intended destination. The Basic Tier protects your azure infrastructure against the most common DDoS attack types for free and without any configuration changes!
If you need a more secure approach for your services or applications, the Azure DDoS Protection Standard Tier is the right service for you. The DDoS Protection Standard Tier extends the feature set of the DDoS Basic Tier and provides protection for your critical environment.
- Native platform integration: Natively integrated into Azure. Includes configuration through the Azure portal. The DDoS Protection Standard understands your resources and resource configuration.
- Turnkey protection: Simplified configuration immediately protects all resources on a virtual network once the DDoS Protection Standard is enabled. No intervention or user definition is required. The DDoS Protection Standard instantly and automatically mitigates the attack on detection.
- Always-on traffic monitoring: Your application traffic patterns are monitored 24 hours a day, 7 days a week, for indicators of DDoS attacks. Mitigation occurs if protection policies are exceeded.

– Source: Microsoft
- Adaptive tuning: Intelligent traffic profiling learns your application’s traffic over time, and selects and updates the profile that is most suitable for your service. The profile adjusts as traffic changes over time.
- Multi-layered protection: Provides full stack DDoS protection when used with a web application firewall.

– Source: Microsoft
- Extensive mitigation scale: Over 60 different attack types can be mitigated, with global capacity, to protect against the largest known DDoS attacks.
- Attack analytics: Get detailed reports in five-minute increments during an attack, and a complete summary after the attack ends. Stream mitigation flow logs to Azure Sentinel or an offline security information and event management (SIEM) system for near real-time monitoring during an attack.
- Attack metrics: Summarized metrics from each attack are accessible through Azure Monitor.

– Source: Microsoft
- Attack alerting: Alerts can be configured at the start and stop of an attack, and over the attack’s duration, using built-in attack metrics. Alerts integrate into your operational software like Microsoft Azure Monitor logs, Splunk, Azure Storage, email, and the Azure portal.
- DDoS Rapid Response: Engage the DDoS Protection Rapid Response (DRR) team for help with attack investigation and analysis. To learn more, see DDoS Rapid Response.
- Cost guarantee: Data transfer and application scale-out service credits for documented DDoS attacks.
Azure DDoS Protection Standard is simple to activate and to use in your existing landscape. Combined with security best practices and application design best practices, it protects you against the impact and consequences of an DDoS attack. To use the DDoS Protection Standard in combination with applications, you need an additional security component: the “Azure Application Gateway”.
Load balancing is an important feature for protecting you web applications and services. Load balancers detect the health of your resources and control which resources receive requests. In Azure you should use the Application Gateway to complete your security set related to web applications and services. The Application Gateway is a web traffic load balancer which operates on the application layer.

– Source: Microsoft
The Application Gateway provides you with a broad feature set for enhancing your security status. Aside from its role in DDoS protection, it enables you to move the encryption and decryption overhead from your servers to the Application Gateway with Secure Sockets Layer (SSL/TLS) termination or with the benefits of autoscaling. In addition, you can span multiple availability zones (zone redundancy) for better fault resiliency. But the most important feature is the Web Application Firewall (WAF). (True, there are many other features, but the WAF is indispensable for protecting your web applications!)
Azure Web Application Firewall
The WAF is a centralized protection feature against common exploits and vulnerabilities, which are often exploited by Script Kiddies and automated attacks to cause damage.

– Source: Microsoft
It’s hard to protect your applications against such attacks. Secure coding is difficult and recruiting staff for implementing secure code seems impossible. The centralized Azure Web Application Firewall masters this challenge for you and eliminates the OWASP TOP 10!
Following our trip to the future, we now travel back to the past to talk about firewalling.
Back to the Past
Last time we talked about micro segmentation and how to protect your networks in Azure, but not how you can protect the edge of your network or your complete VNET (NSG segment subnets, not VNET!).
To close this gap, you can use the Azure Firewall.

– Source: Microsoft
Azure Firewall is a managed, cloud (native) based service. It is a stateful firewall with built-in high availability. The Azure Firewall enables you to create, enforce and log application and network connectivity policies. The features include application FQDN filtering rules, network traffic filtering rules, threat intelligence, outbound SNAT support and inbound DNAT support. In addition, the Azure Firewall is certified for PCI, SOC and ISO.
The best practice in using the Azure Firewall is to place it in a HubVNet.
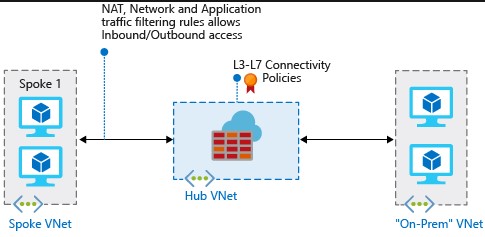
– Source: Microsoft
This approach ensures that all traffic will flow through the firewall, and it enables you to control the traffic from one network to another. In combination with the feature set of the Firewall Service, it blocks traffic from malicious sources and generates an overview, giving you full control over your network!
Bringing the Azure Firewall in line with your NSG/ASG and enhancing it with an application gateway and DDoS protection will ensure your successful travel to a secure future!
Author: Dominic Iselt, IT Security Engineering Expert
